Wifite is not maintained, it's Wifite2. It is complete rewrite of previous popular tool wifite2 by derv82, thanks to kimcoder to maintain this repository well. It's designed to automate the process of a wireless auditing. To run properly it needs Aircrack suit, Reaver, Pyrit and some more to be installed. Wifite and the additional tools to run it comes pre-installed with Kali Linux (if not then we can simply apply sudo apt install wifite -y command to install it).
Features of Wifite
With the help of wifite we can audit WEP, WPA, WPS encrypted network by by multiple attacks. Before using this powerful tool we gonna check it's features:
- Wifite can shorts targets by signal strength that means we can crack the good signal or the closest access points first.
- It can automatically de-authenticate clients of hidden networks and then reveal their SSID's.
- "anonymous" features, wifite can generate a random MAC address before attacking and after attack it comes back to original MAC. We have did this manually in our Changing MAC Address tutorial.
- We can skip an attack by Ctrl+C and it will start the next attack.
- Wifite saves all cracked passwords in text file.
Using Wifite on Kali Linux
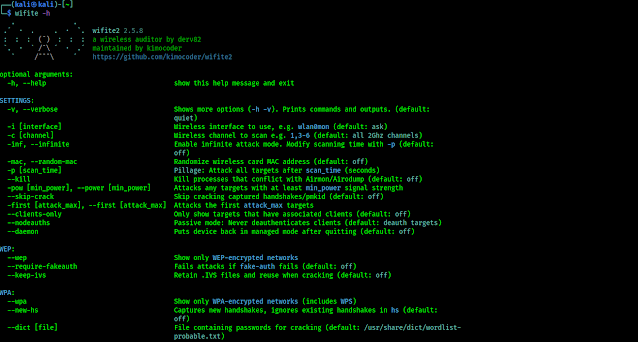
We need t open our terminal window and run following command to start Wifite's help options:
In the following screenshot we can see the output of the above command:
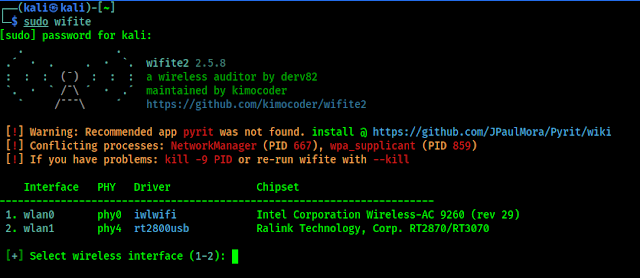
Here we need to keep in mind that we must plug on our monitor mode and packet injection supported Wi-Fi adapter with our system, to audit wireless systems using Wifite. We can start using it by simply using following command:
We can see the output in the following screenshot:
Here we need to select our wireless interface (In our case it is #2, it is our external WiFi adapter), so we press 2 and hit Enter ↲. In the following screenshot we can see that Wifite turns on Monitor mode and scanning for targets:
Here we can stop the scanning process if we got our target Wireless network by pressing CTRL+C. (Here we got a our home WiFi nothing more).In the following screenshot we can see that we need to select our target network or we can say all and press Enter ↲ for auditing all wireless networks found.
Then Wifite will start auditing the wireless network(s), It will start from capturing handshakes, then automatically try to crack the handshake file using a default wordlist (/usr/share/dict/wordlist-portable.txt). As we can see in the following screenshot:
Now this default wordlist is not enough to crack our password (after-all we are working on cybersecurity). If we want to use another wordlist then we can try following command to run wifite:
In the following screenshot we can see that wifite is going to use our mentioned wordlist for cracking handshake file.
If we want to use pixie dust attack using wifite then we should use command sudo wifite --bully (Use bully program for WPS PIN & Pixie-Dust attacks) or sudo wifite --reaver (Use reaver program for WPS PIN & Pixie-Dust attacks). To attack access points with over 50 dB of power (-pow 50) using the WPS attack (-wps), and command will be sudo wifite -pow 50 -wps.
We can see all other options on the help menu (wifite -h), and learn how we can use wifite tool.
Warning: This article is written for educational and security awareness purpose. Damaging others is not ethical and may be consider as offensive crime. We don't support any unethical works. All the tests in this article is done at our own lab by attacking our own devices.
Wifite is an automated WiFi cracking tool on Kali Linux, we just need to run wifite, select our targets, and Wifite will automatically start trying to capture or crack the password or other attacks.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.