During penetration testing of a website or web application we must need to gather information as much as we can about our target. Gathering DNS information is also must be do for a security expert.
In today's article we are going to cover dnsX, it's a tool created by projectdiscovery. It is a fast and multi-purpose DNS toolkit allow to run multiple DNS queries of our choice with a list of user-supplied resolvers. It also supports DNS wildcard filtering like shuffledns. We will learn about installing dnsX on our Kali Linux system and use it.
Key Features of dnsX
- Simple and Handy utility to query DNS records.
- A, AAAA, CNAME, PTR, NS, MX, TXT, SOA query support.
- DNS Resolution / Brute-force support.
- Custom resolver input support.
- Multiple resolver format (TCP/UDP/DOH/DOT) support.
- stdin and stdout support.
- Automatic wildcard handling support.
Installing dnsX on Kali Linux
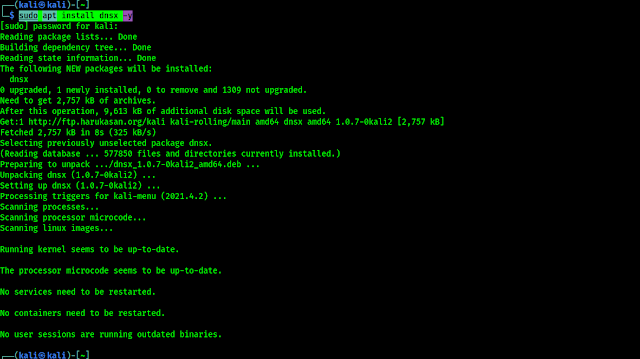
After 2022.1 update of Kali Linux dnsX is added to Kali Linux repository, so the installation will be hassle-free, we just need to run the following one liner command on our terminal:
In the following screenshot we can see the output of the above command:
Done! dnsX is successfully installed on our Kali Linux system.
Using dnsX on Kali Linux
Let's start with the help section of dnsX tool. To check the options we run the following command:
In the following screenshot we can see the help options of dnsX tool:
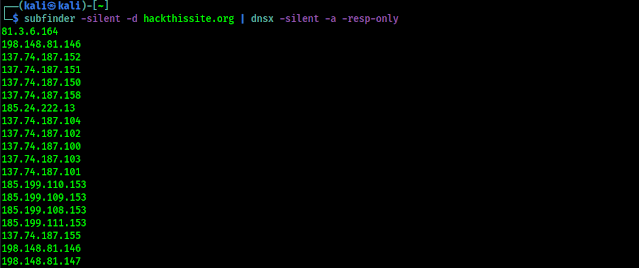
Now let's start using it with an example, here we have a list of subdomains we can run the following command to check for active subdomains:
let's suppose we found some subdomains using Subfinder, now we can easily check for active subdomains from the list of passive subdomains we got from various sources. Following command will be an example:
In the above command we used -silent flag to keep our terminal clean. The command will take some time to collect all the data. We can see the output of the above command in the following screenshot:
Also dnsX can be used to print A records, for an example:
In the following screenshot we can see the A records with the subdomains:
Also it can extract only the A records. To do so we run the following command:
Now it will extract A records only, as we can see in the following screenshot:
dnsX can be used to extract CNAME records, for an example:
We can see the output in the following screenshot:
We can see the dns status codes by using dnsX tool, as we did in the following command:
Following screenshots shows the output of the applied command:
This dnsX tool also can perform bruteforce subdomains for given domain or list of domains using -d and -w flag, for example we can check this.
Extra Talks
- By default, dnsx checks for A record.
- By default, dnsx uses Google, Cloudflare, Quad9 resolver.
- Custom resolver list can be used using -r flag.
- Domain name (-wd) input is mandatory for wildcard elimination.
- DNS record flag can not be used when using wildcard filtering.
- DNS resolution (-l) and DNS Bruteforcing (-w) can't be used together.
This is how we can use dnsX tool on Kali Linux, and collect DNS information for security testing.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.