Lynis is a free open-source security auditing tool for systems based on UNIX like Linux, macOS, BSD, and others. It performs a security scan and runs on the system itself.
In this tutorial we learn how we can scan our Linux (read Kali Linux) system to fix it's vulnerability and know is there any malware in our system.
Lynis is created by Michael Boelen, Michael Boelen is the creator of Rkhunter.
Lynis is created for in-depth security scan on internal system and give tips and suggestion. This tool is very useful for auditors, security specialists, penetration testers, and sometimes system/network administrators.Key Features of Lynis
The main goals are:
- Automated security auditing
- Compliance testing (e.g. ISO27001, PCI-DSS, HIPAA)
- Vulnerability detection
Lynis (also) assists with:
- Configuration and asset management
- Software patch management
- System hardening
- Penetration testing (privilege escalation)
- Intrusion detection
Install & Update Lynis in Kali Linux
Lynis comes pre-installed with Kali Linux full version or we can install/update it by using following command:
After this we can see help options of lynis by using following command:
We can see lynis help menu in the following screenshot:
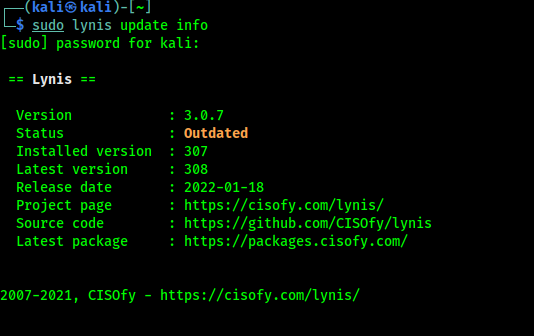
Now we can check if our Lynis is updated or not? To do that we use following command:
The output of the command in following screenshot:
In the above screenshot we can see that our Lynis (version 3.0.7) comes with Kali Linux is outdated. So we clone it directly from it's GitHub repository by using following command:After the cloning process complete we go to lynis directory by using cd command:
From here we can run lynis. We check the update information here by using following command:
In the following screenshot we can that we got the updated Lynis.
Yes, now we got the latest version 3.0.8. Now let's use it.Using Lynis in Kali Linux
We can use Lynis to audit our local system and remote system. We also can analyze Docker files using Lynis. For an example we just scan our Kali Linux system for now.
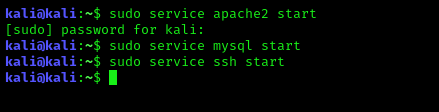
Before starting the audit to get better result we run some services on our system.
Here we start our Apache web server, Mysql databases and ssh services. To start them we need to run following three commands on terminal:
Now we are ready to run audit on our system. To perform a scan/audit we need to run following command:
After this the auditing will run. This will take just around a minute depending on system's performance.
Now our above audit was a non-privileged scan. Means we don't give it root permission. But whenever we scan without root permission the auditing process will not scan the root system. So if we need we can perform the audit with root by using following command:
Then it will ask us the sudo password and then we need to confirm the process by pressing "Enter".
To scan a remote host we can use following command:
Analyzing Results
Now we analyze the results of our auditing. So our report-data is shown in our terminal and also it stored in /var/log/lynis-report.dat file.
The following screenshot shows the results of Lynis audit:
In the above screenshot we can see Lynis gives us some warnings and lots of suggestions to make our system safer and secure.
All the issues carries a ID like we took a PHP error warning's ID is [PHP-2376].
Now to know more about this warning and how to fix it we can the given web link or see this ID's details by using following command:
Here Lynis gives us the solution how we can fix this error, we can see the highlighted area in the following screenshot:
When Lynis starts scanning our system, it will perform auditing in a number of categories:
- System tools: system binaries
- Boot and services: boot loaders, startup services
- Kernel: run level, loaded modules, kernel configuration, core dumps
- Memory and processes: zombie processes, IO waiting processes
- Users, groups and authentication: group IDs, sudoers, PAM configuration, password aging, default mask
- Shells
- File systems: mount points, /tmp files, root file system
- Storage: usb-storage, firewire ohci
- NFS
- Software: name services: DNS search domain, BIND
- Ports and packages: vulnerable/upgradable packages, security repository
- Networking: nameservers, promiscuous interfaces, connections
- Printers and spools: cups configuration
- Software: e-mail and messaging
- Software: firewalls: iptables, pf
- Software: webserver: Apache, nginx
- SSH support: SSH configuration
- SNMP support
- Databases: MySQL root password
- LDAP services
- Software: php: php options
- Squid support
- Logging and files: Syslog daemon, log directories
- Insecure services: inetd
- Banners and identification
- Scheduled tasks: crontab/cronjob, atd
- Accounting: sysstat data, auditd
- Time and synchronization: ntp daemon
- Cryptography: SSL certificate expiration
- Virtualization
- Security frameworks: AppArmor, SELinux, security status
- Software: file integrity
- Software: malware scanners
- Home directories: shell history files
Conclusion
We can check the configuration flaws in above wide categories. Many tests are part of common security guidelines and standards, with on top additional security tests. After the scan a report will be displayed with all discovered findings.
Lynis also have a more useful paid version. To know pricing and more please check here.
Here we can see how we can fix issues with our system. Lynis also able to find malwares in our system. This tool is very useful for protecting a Unix based system. This is how we can do a security audit on Kali Linux using Lynis & make our system secure.A safer system for a safer world.
Liked our tutorial then follow our blog from the right-sidebar using e-mail id. Also we are in GitHub and Twitter. We post updates there.
For any problem or question please feel free to comment down below we always reply.