During penetration testing works we need exploits to penetrate into some system, writing an exploit is really a time-consuming job. It is also difficult to find a publicly available exploit for our exact need. So the easier way is we modify the publicly available exploit for our specific work.
In the case of memory corruption exploits (like buffer overflows), we need to modify some basic target parameters like target information, return IP address, payload and offset.
But this will not work in every situation, suppose if our target is running Windows server 2012 and we are trying to run an exploit that was created for Windows server 2008. It will be funny because things are changed, newer patches are updated, we should avoid doing that.
We always choose right version of exploit and if possible we read the codes and try it on a sandbox system (same system as target in our virtual machine). Then we need to use that exploit.If we know about the target system then we can search for the exploits can run on it. Here we are talking about publicly available exploits. We can search exploits in both online and offline environment.
Online Exploit Libraries
Many online exploits resources are available they stores exploit codes and make it available for public. Here we talk about some best online resources for exploits.
The Exploit Database
Exploit Database is a project maintained by Offensive Security. It is a free archive of public exploits. These exploits are gathered from submission, mailing lists and public resources. Sometimes ExploitDB provides the installer for the vulnerable version of the application with exploit for testing and research purpose.
When the vulnerable version of application installer is available with exploit there will be a A mark (as shown in the following screenshot) on the ExploitDB website. For practice and research uses we like this.
 |
| Exploit DataBase |
If we want to get notified about the most recent exploits then we need to follow their Twitter. We also posts about cybersecurity to get notified also follow our Twitter.
Packet Storm
Packet Storm is very senior. It was established in 1998. It provides updated information on security news and vulnerabilities. It also keep us updated on recently published security tools.
 |
| Packet Storm Homepage |
Packet Storm also have Twitter, Facebook and RSS feed to follow and stay updated on new news.
SecurityFocus
SecurityFocus exploit archives was created in 1999 and still it is focused on some few key areas important to the security community.
- BugTraq: BugTraq is a full disclosure mailing list with the purpose of discussing and announcing new security vulnerabilities.
- SecurityFocus Vulnerability Database: This is a archive that provides up-to-date information on vulnerabilities for all platforms and services.
- SecurityFocus Mailing Lists: This is a topic-based mailing lists allow researchers around the glove to discuss on various security loopholes.
Google Search
We can find our required exploit from the "Google Search". Google is the most popular search engine (WoHA, told something secret🤪).
We can start searching for a specific software version with the exploit keyword, that's it. we also can include various search operators that can help us to find what exactly we want.
For an example we need exploits for "Internet Explorer" browser and we want only exploits hosted on Exploit DataBase's website then we can use this search query on Google 'Internet explorer site:exploit-db.com'. As shown in the following screenshot.
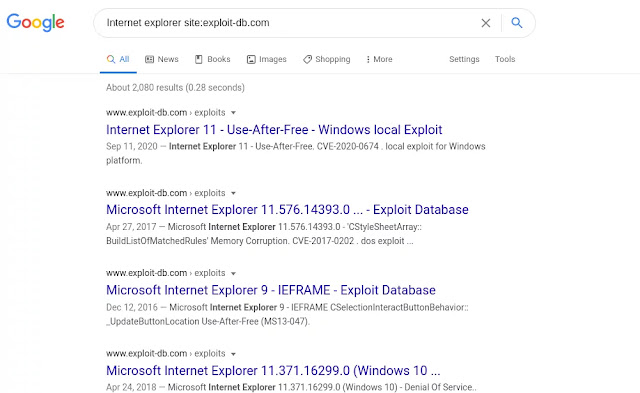 |
| Searching for Exploit |
In this way we also can use some other search operators if require, like "inurl", "intext", "intitle".
We need to be careful when we run exploits from non-trustable resources, we need to read the exploit carefully, because it might harm our system.
Offline Exploit Searches
If we are in some other place where we might not get the internet to search exploits. In cases where the assessment takes place in an isolated environment, Kali Linux comes with various tools that provide offline access to exploits.
SearchSploit
Exploit Database provides a downloadable archived copy of all the hosted exploit code.
The archive comes by default in Kali Linux in the explotdb package. Here to get the latest exploits we need to keep this package updated whenever we can. To update this package we can apply following command:
Then our exploitdb package will be updated and we got a local copy of Exploit Database archive. We can found the exploits on /usr/share/exploitdb directory. Here we got exploits and shellcodes.
But without searching exploitdb exploits manually (time-consuming process) we can use the searchsploit utility.
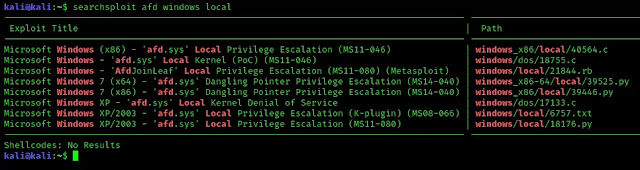
We can run searchsploit from the terminal. For an example we run following command in our terminal.
The screenshot of the command is following:
In the above screenshot we can see the exploits the locally hosted locations of the exploits and their paths.
Nmap Scripting Engine (NSE) Scripts
Nmap is the most popular tool for scanning and enumeration. One very powerful function of the tool is the Nmap Scripting Engine. As in the name we can see automate lot of tasks automatically.
We can do enumerate, brute force, fuzz, detect even exploit services.
These scripts are located in /usr/share/nmap/scripts directory. Let's move to the directory using cd command.
Here we can use grep to search quickly the 'exploit' word into those scripts.
In the following screenshot we can see the list of exploits.
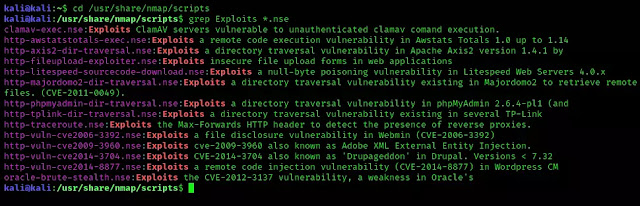 |
| Nmap exploits |
We also can see the information on specific NSE scripts by running --script-help option with nmap command. An example is following.
 |
| Opening help of a Nmap exploit script |
BeEF
Browser Exploitation Framework or BeEF is a cybersecurity tool used on client-side attacks executed in target web browser. It also includes various exploits. We have discussed about BeEF on our previous article.
Love our articles? Stay updated with our articles by following us on Twitter and GitHub. Be a part of the KaliLinuxIn community by joining our Telegram Group, where we focus on Linux and Cybersecurity. We're always available to help in the comment section and read every comment, ensuring a prompt reply.