Android is the most popular mobile operating system in our world. It is open-source. But there are numerous malware, spyware etc available for Android. Google still have very easy policy to list any application on Play Store so we can't trust play store blindly. Many times Google banned various applications from play store due to using malicious activities. We can't blindly trust any brand, to be totally safe we need check every app our self before installing it on our phone.
That's what DroidDetective does. It's a machine learning malware analysis framework for Android apps. DroidDetective written in Python and it is used for analyzing Android applications (APKs) for potential malware related behavior and configurations. When provided with a path to an application (APK file) Droid Detective will make a prediction (using it's ML model) of if the application is malicious.
Key Features of DroidDetective:
Some main features of DroidDetective is following:
- Analysing which of ~330 permissions are specified in the application's AndroidManifest.xml file.
- Analysing the number of standard and proprietary permissions in use in the application's AndroidManifest.xml file.
- Using a RandomForest machine learning classifier, trained off the above data, from ~14 malware families and ~100 Google Play Store applications.
Install DroidDetective on Kali Linux
Now without wasting much time we are going to install DroidDetective on our Kali Linux system. First of all we need to clone DroidDetective's GitHub repository by using following command:
In the following screenshot we can see the output of the above command:
After that we need to go inside the DroidDetective directory by using following command:
Now we need to fill up all the requirements to run this tool by using following command:
The following screenshot shows output of the above commands:
Now our installation process is done. It's time to find potential malwares our Android applications.
Using DroidDetective on Kali Linux
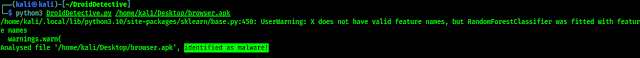
First we need to have a APK file to test using DroidDetective. We have an APK file named browser.apk on our Desktop directory so we need to apply following command to start analyzing it:
We can see the output for the above command in the following screenshot:
That was a malware and DroidDetective found that there is some suspicious things within this malware. We can also saves the output in a json file by usng following command:
This is how we can find if there is any malware or other malicious things inside an APK file.
Something More
During the testing we noticed that some APK which doesn't contain malicious things also get detected by this tool due to misconfiguration or for some permission requirements. We need to take care of this. Someone familiar with Android development can easily figure out what's wrong using DroidDetective, they doesn't need to read the whole program.
To know more about how DroidDdetective's pre-trained model works to find malware we can go to ashisdb's repository. More information we can see at DroidDetective GitHub repository.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.